Perimeter Protection in Airports: How Isarsoft Perception uses Video Analytics to enhance Safety
Airports and airport runways are safety-critical zones, subject to rapid movement made by people, machines, and vehicles. In cases of flight loading, boarding, and disembarkation, there are certain zones that are marked classified or prohibited for purposes of security enforcement. This is where the concept of perimeter protection comes in. In this article, we conduct an examination of how Isarsoft Perception enforces perimeter protection norms in airports.
Published
June 19, 2023

Introduction
What is Perimeter Protection?
Perimeter protection refers to the safeguarding of an area, building or facility by means of security personnel, CCTV cameras, alarms, and motion sensors. It is done in order to implement safety protocol in the context of unauthorized access, confidentiality, and the detection of potential threats that can hamper information, machinery, or human lives.
In this article, we take the example of an airport. Perimeter protection could be applicable to several areas within an airport - runways, parking facilities, terminals, and cargo facilities. Maintaining a constant standard of security is very important in airports, which is why perimeter protection becomes especially relevant.
Traditional Methods vs. Modern Methods
Traditional Methods
Before technology and associated functions developed as much as it has, the methods for perimeter protection used to be largely based on human-oriented structures. Security in the form of patrolling officers were a common choice, as were electric fences and walls designed to keep out intruders from areas that were classified. Old-fashioned alarm systems were also used, using a variety of technical and electrical components that predated modern tech. Some of them were:
- Mechanical contact - Mechanical contact-based security systems used pressure mats and door/window sensors to detect the presence of an unauthorized person. When triggered, the mechanical contact would proceed to physically close a circuit.
- Alarm bells - Alarm bells were a popular choice for security systems, with a loud 'alarm' sound being the indicator of the security breach.
- Telephones - Telephones lines could be rigged to the in-house security system, with a pre-programmed call being made to the security office in case of the alarm being triggered.
Modern Methods
Technology has, of course, come a long way since. The above methods soon evolved into methods that made use of wired connectivity, control panels, and key switches. With the advent of smart technology and intelligent analytics, the ways for perimeter protection have been further strengthened. Some of the common tools in use today are:
- Motion Sensors - A motion sensor is an electrical device that is programmed to detect and measure nearby movement.
- Thermal Imaging Cameras - Thermal imaging cameras are similar to normal cameras, except that they use infrared radiation to form an image instead of visible light. They can be used to detect objects in the vicinity by identifying and registering temperature fluctuations ( unauthorized human access can be clocked by detecting body temperature), and taking an image.
- Intelligent Video Analytics - Intelligent video analytics is a tool that utilizes camera streams to monitor the situation, and provide relevant insights.
- Intrusion Detection Systems (IDS) - An intrusion detection system is a software or application that is tasked with monitoring a network for policy violations, malicious activity, or any other kind of intrusive activity.
- Access Control Systems - Access control systems are electronic in nature, and facilitate automated approval for personnel who have been authorized. This is done by typically using credentials that allow access without the presence of a security officer. These systems can control entry and exit to and from the concerned facility.
- Radar Systems - Radar is a radio-location system that takes the help of radio waves to ascertain factors such as distance, angle, and radial velocity of a specific object or objects w.r.t the site of observation.
How does Video Analytics play an important role?
Video analytics is an integral part of smart security systems. Of the many ways to supplement perimeter security at airports which include motion sensors, thermal imaging cameras, physical barriers such as fences and walls, and devices that detect an intruder - video analytics is one of the most effective.
The reason for this is two-fold:
- Automated Monitoring - Intelligent video analytics can run monitoring feeds without human intervention. Live or recorded data footage can be monitored consistently, in order to ensure a constant state of watchfulness that is essential to the guarantee of safety.
- Operational Insights - Video analytics can be used to generate relevant insights about detected objects in terms of KPIs such as speed, dwell time, trajectory, etc.
How does Isarsoft Perception conduct Perimeter Protection?
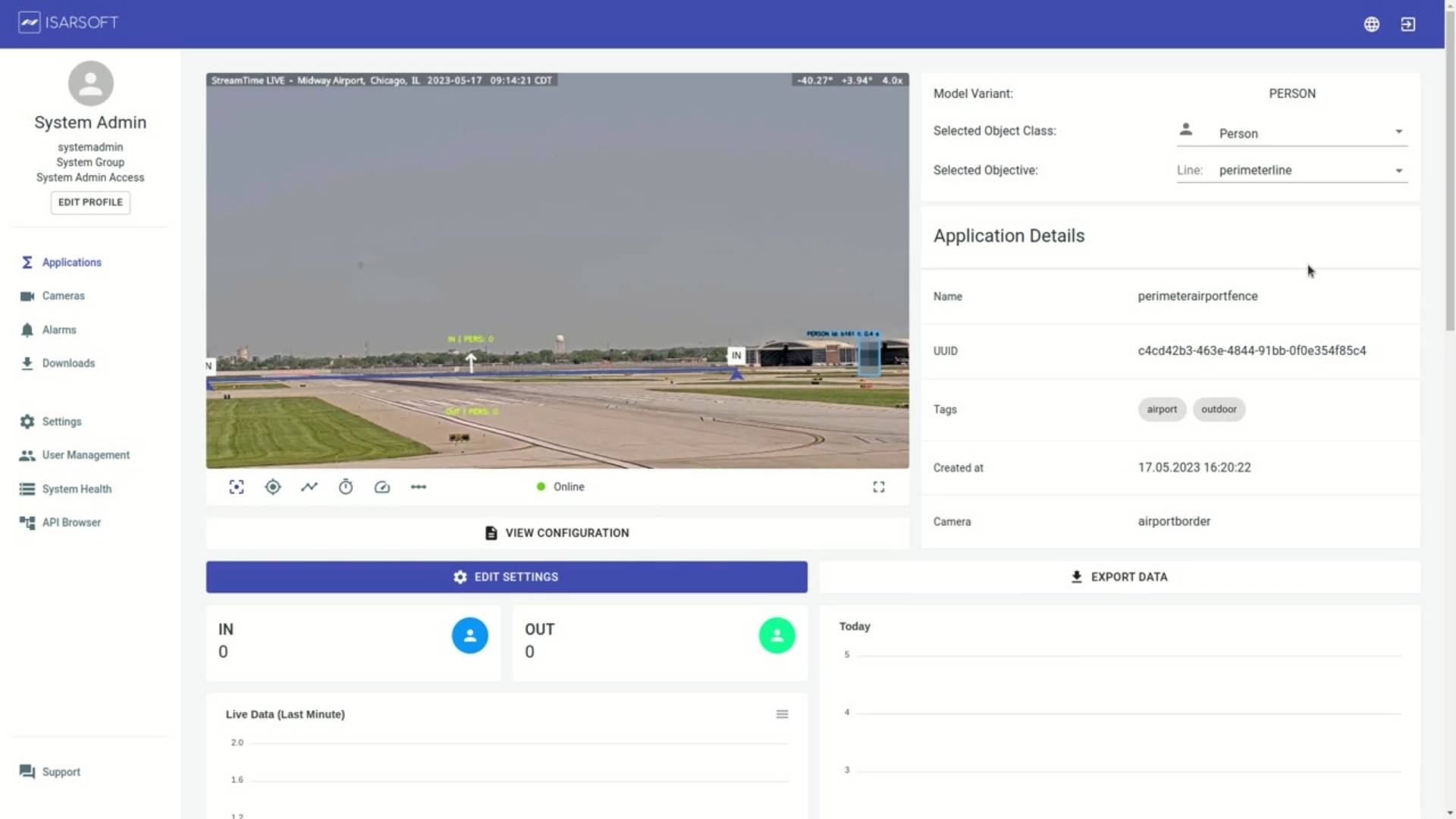
Isarsoft Perception when operating in the aviation sector has a wide range of functionality in terms of planning, optimization, and security. Perimeter protection can be performed through the creation of an Object Flow application. It is designed to identify and detect objects, measure volume (via the creation of a line), measure density (via the creation of a zone), and analyze KPIs such as speed, trajectory, and dwell time using a range of maps.
The creation of a line bears especial relevance.
By creating a line, areas/zones can be marked out to ensure further processes. Lines can be created by adding a new line to the desired area. Each line is bookended by two clickable points, that can be extended to cover the required length. Every line can be modified to add direction.
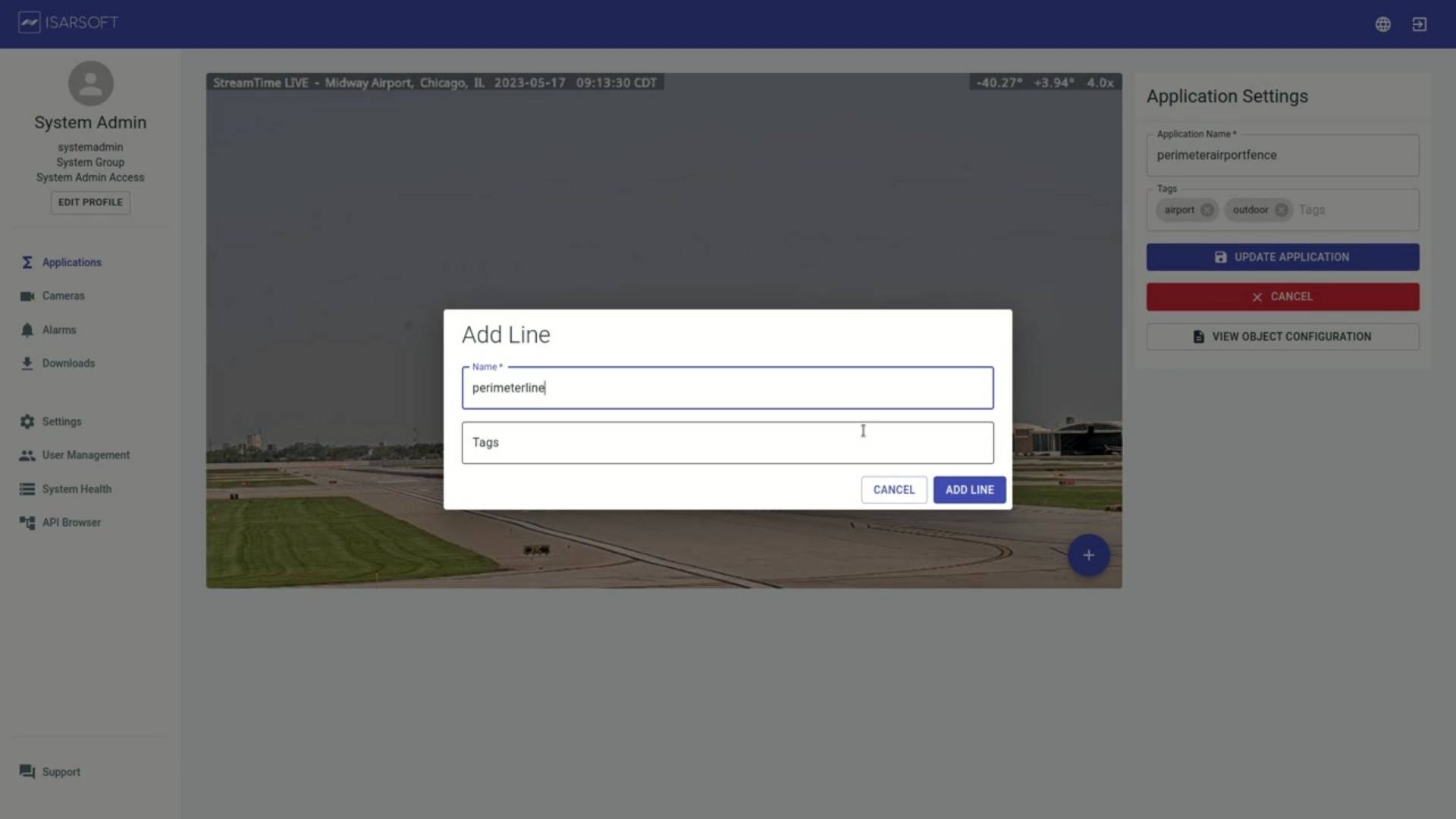
When creating a new line on the Object Flow application, the line can be named and flagged with relevant tags to aid the user in better defining the purpose and circumstances of the line in question.
The line, once created, can now be used to measure the number of pedestrians or vehicles that pass through it.
Benefits of Isarsoft Perception for Perimeter Protection
Real Time Detection
Isarsoft Perception identifies and detects objects in real time. Especially useful for security purposes, adequate perimeter protection can be instated through the use of the software. In addition, the processing of collected data also takes place live - ensuring that users do not have to wait to access security updates, consequent analysis, and other relevant data.
Automatic Anonymization
Isarsoft Perception provides automatic anonymization of camera streams. This is important for reasons of privacy protection because an anonymized camera stream removes all personal identifiers of the detected objects. In high-security areas such as airports, it is important that information be handled sensitively. In addition, Isarsoft is compliant with GDPR regulations, and includes the necessary configurations required to protect users' private data.
Automatic anonymization ensures that the analysis of the collected data can take place unhindered, without compromising any personal information. Anonymized data still retains valuable insights required for further analysis.
Alarm-setting Feature
Isarsoft Perception offers to users the option to create an alarm within the software, set to be triggered by user-defined factors. This can be used to detect potential threats and do the needful immediately.
Anomaly Detection
Isarsoft Perception can be used to access relevant, KPI-based insights. The live data generated by the software is displayed in the form of a graph. The visual medium of display aids quicker comprehension, and can help users identify anomalies through sudden crests or troughs.
By displaying data visually, Isarsoft Perception's user interface becomes more intuitive and thereby, easier to use. Users no longer have to sort through huge volumes of data in order to identify an anomaly - they can just look at a graphical image to gain a speedy overview.
Integration with Safety Systems
Isarsoft can be seamlessly integrated with safety systems.
Future Developments and Trends
The future of perimeter protection via video analytics or other intelligent sensing devices promises to be stronger. Video analytics are set to improve and evolve over time, and be able to categorize unauthorized access or intrusions by a variety of means. Some of the methods already in use include detecting potential threats based on analysis of movement, trajectory mapping, and flagging a problem if a detected object remains stationary for too long.
Video analytics tools can be deployed in a combination of internal and external locations to be better equipped to deal with intrusions, and raise alarms even before the perimeter has been breached.
More about Isarsoft
With Isarsoft Perception, your camera systems become part of your business intelligence. Whether the goal is to increase efficiency, customer satisfaction or safety, Isarsoft Perception provides the insights needed for informed decisions.

Contact us, to learn more about how to turn security cameras into intelligent sensors.
Further References
Optimize your business processes.
Improve business processes with video-based business intelligence from Isarsoft.







.png)

.png)